Analyzing a PJL directory traversal vulnerability – exploiting the Lexmark MC3224i printer (part 2) : r/netsec
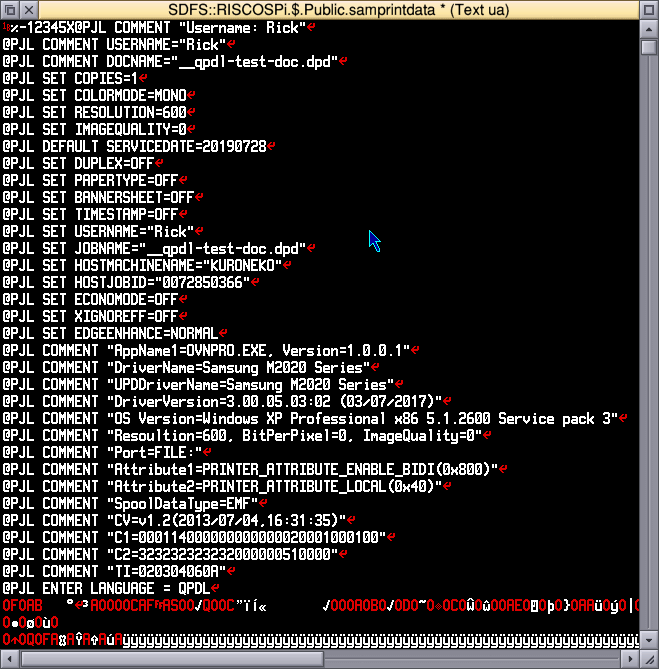
GitHub - your-favorite-hacker/pjl-tool: printer job language tool, for accessing the filesystem, checking for data like documents, faxes or similar

Why is my EPSON L130 printer printing pages with lines all starting with "@JPL" when I connect it to my new Windows 10 laptop computer? - Super User