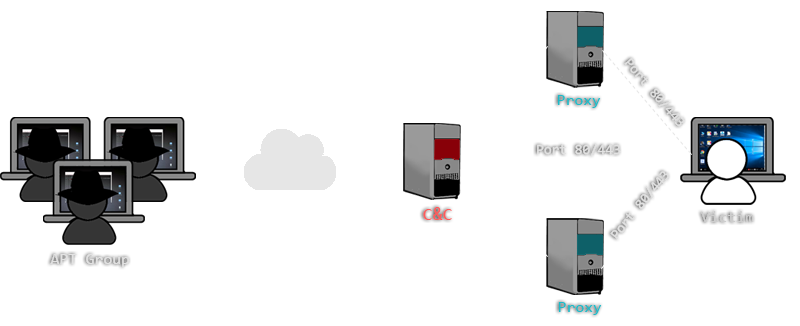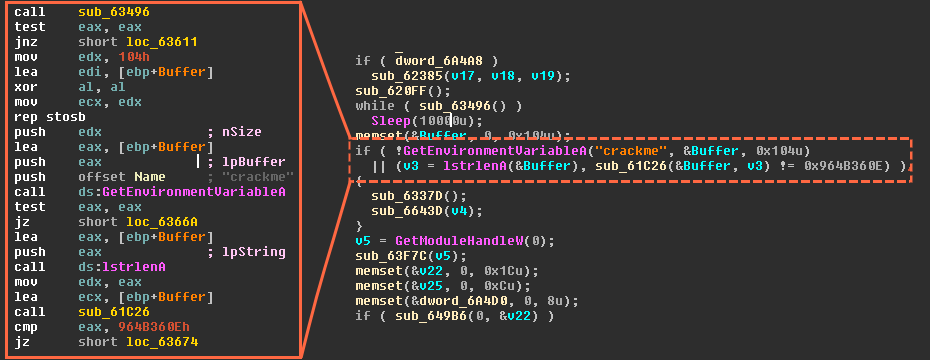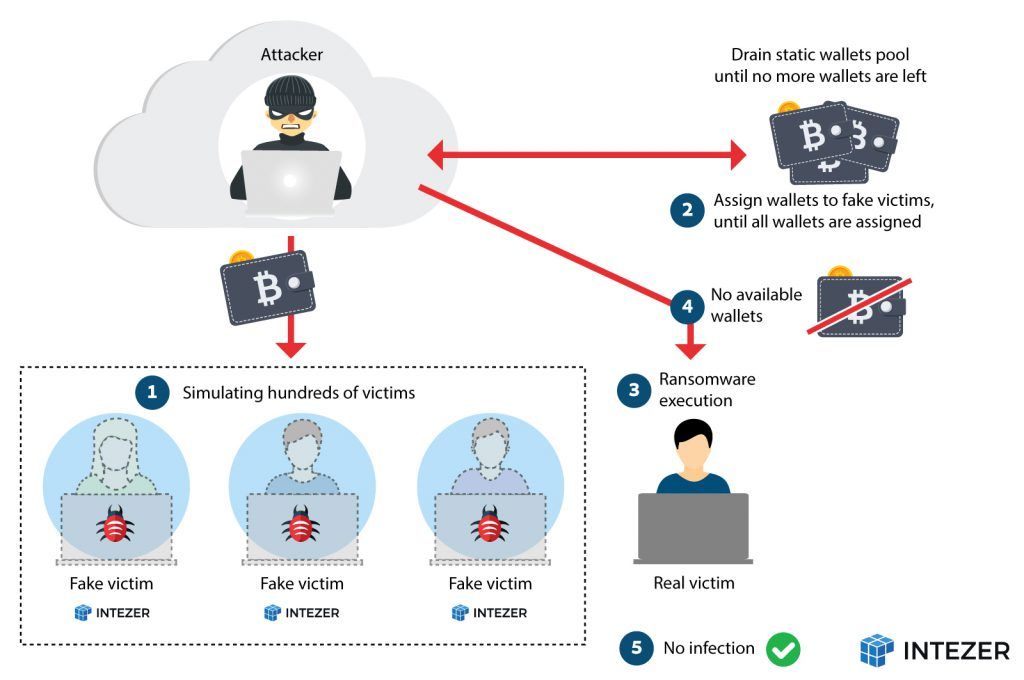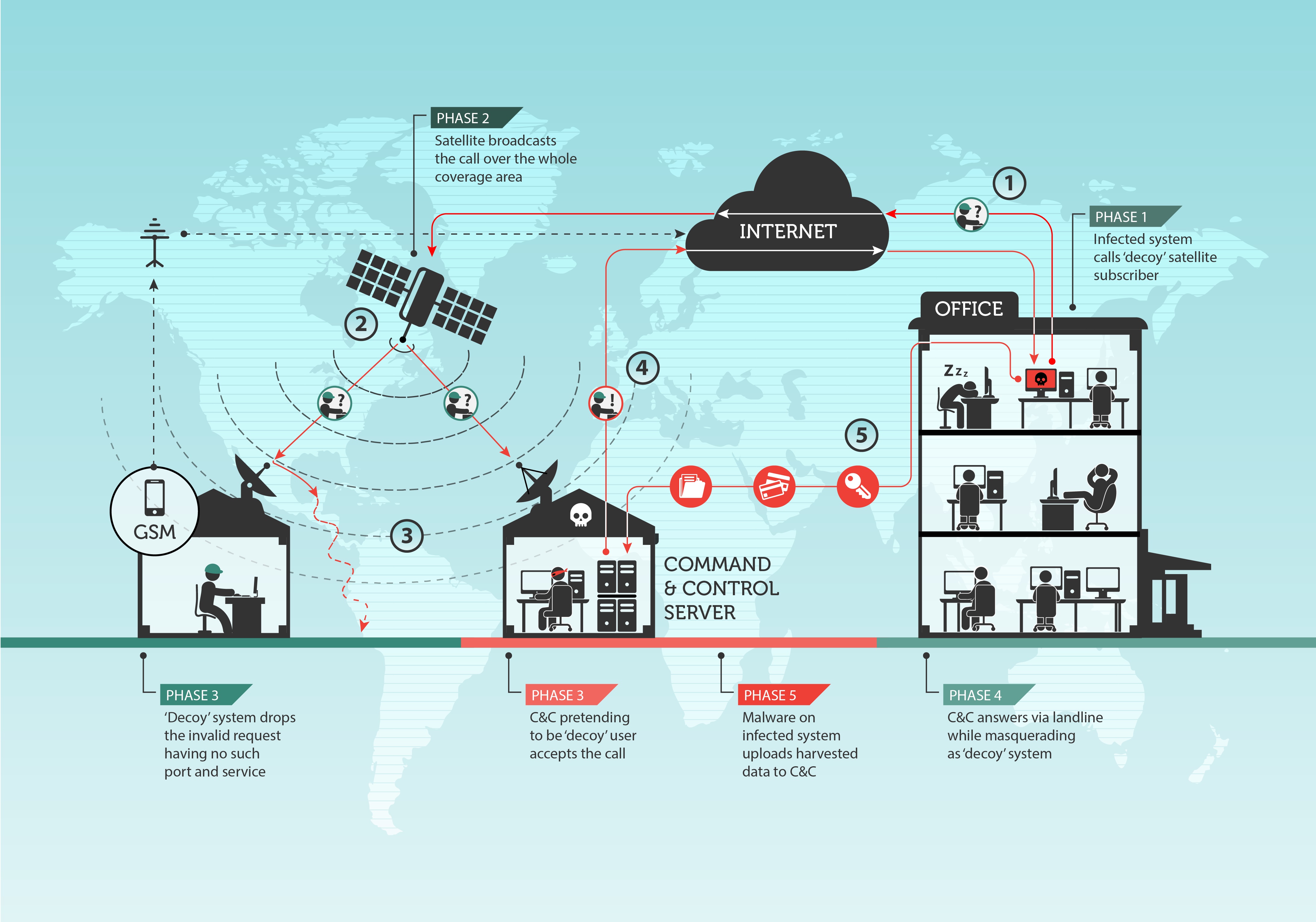
Turla In The Sky With Satellites: Cyber-Espionage Group Hides C&C Server Locale IT Voice | Online IT Media | IT Magazine

Obtain C&C Channel. Command and Control is a key role to… | by Mohans | Redteam & Blueteam Series | Medium

ESET research on Twitter: "#Evilnum uses several malicious components in its attacks. Each operates independently and has its own dedicated C&C server. The JS backdoor initially compromises the system and other components