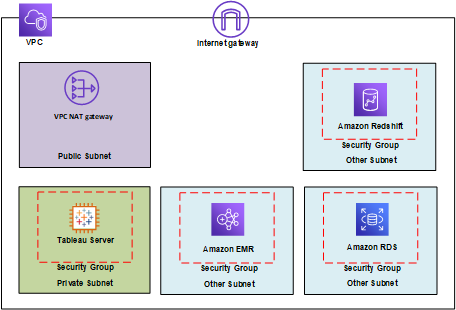
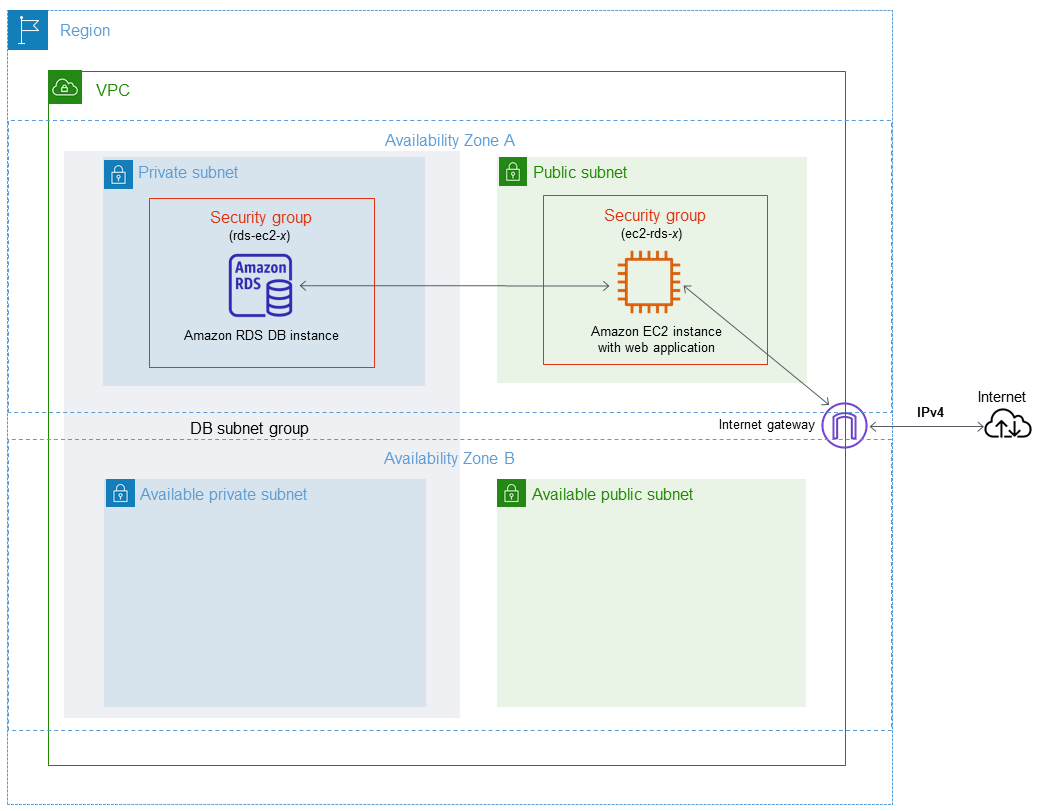
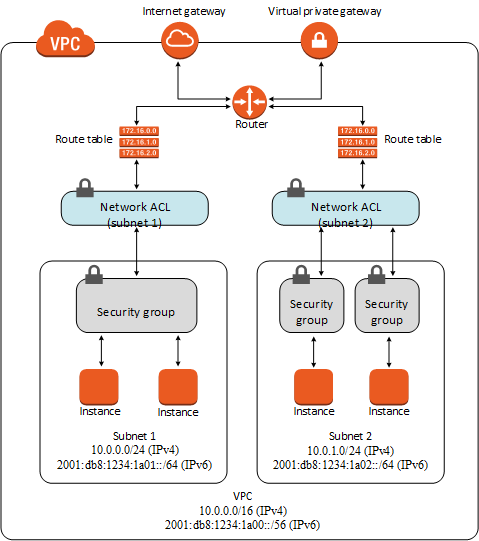
Implementing security notifications for end user activity on Amazon FSx for Windows File Server | Windows on AWS

How AWS Managed Microsoft AD Helps to Simplify the Deployment and Improve the Security of Active Directory–Integrated .NET Applications | AWS Security Blog

Use EC2 Instance Connect to provide secure SSH access to EC2 instances with private IP addresses | AWS Security Blog